Table of Content
I2P, an overlay network used to browse the Internet anonymously. Bitcoin and additional corresponding to Ether, Nxt and Peercoin are peer-to-peer-based digital cryptocurrencies. See Wikipedia's guide to writing higher articles for ideas. Needs to review the safety of your connection before proceeding. ☑The Nessus Attack Scripting Language permits safety analysts to quickly create their own plugins for vulnerability checks.
The server on this state of affairs is most likely going a dedicated sport server, purely targeted on simulating the sport state and relaying data. The textual content following it accommodates the corresponding plain textual content explanation for human consumption. Client software program solely needs to verify the three digits towards an inventory . This indicates that the server has accepted the command and that the consumer can proceed to the next stage. Simple shopper end software program may just respond to 250 codes and ignore the remaining, aborting the session otherwise. In any case, the client must await a reply before continuing to the next stage.
N-tier: Multitier Architecture
2-Tier architectures add a server to the mix and separate the presentation layer to a user interface, where the consumer makes requests outdoors its capabilities. Clients and servers tackle extra enterprise and database logic at varying ranges, providing administrators some control. Ongoing analysis efforts for designing effective incentive mechanisms in P2P systems, primarily based on principles from game principle, are beginning to take on a more psychological and information-processing course. Companies developing P2P purposes have been involved in numerous legal cases, primarily in the United States, over conflicts with copyright law. Two main circumstances are Grokster vs RIAA and MGM Studios, Inc. v. Grokster, Ltd..
A centralized database stores all details about the network. Usually, this information contains consumer accounts, passwords, computer accounts, location of shared sources, access guidelines, and the hierarchy of the network. The system on which the centralized database is installed is called the server system.
What Are Multiplayer Server Models?
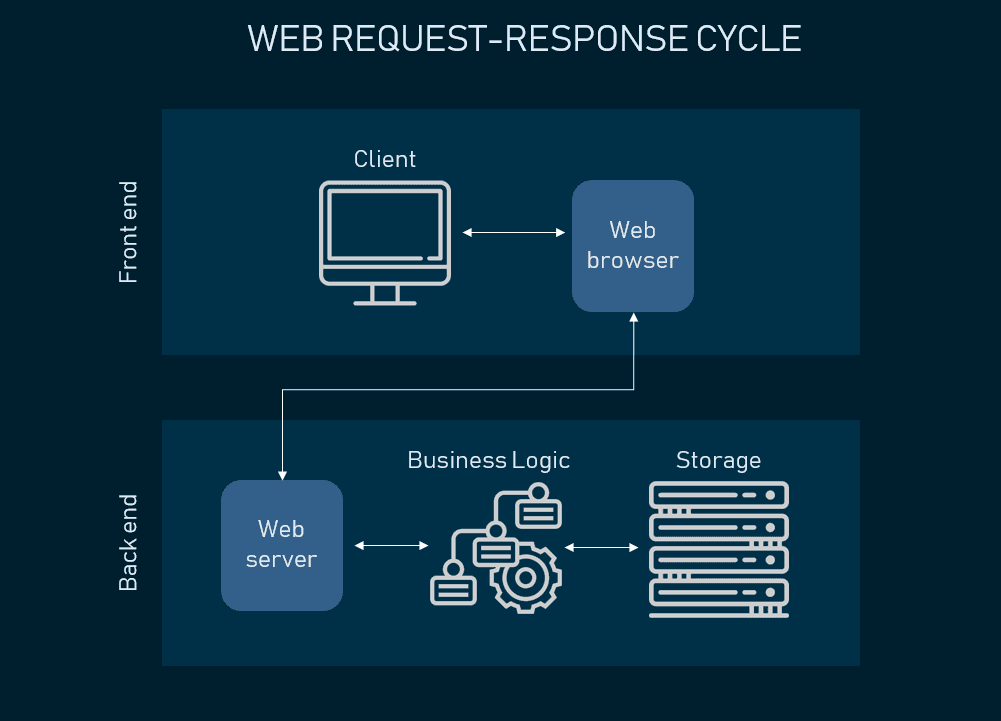
One of the famous examples of a 2-tier design is the web ticket reservation process. The client server model is, in practice, the fundamental working precept of all knowledge facilities together with the cloud. The term “client server model” simply describes a technique in which not all of the necessary purposes and information are put in instantly onto an endpoint. Instead, some or all of these information or apps are installed on a server located elsewhere. Clients, taking the form of laptops, desktops, tablets, or smartphones, then request a file or application from the distant server. The server hears the request, verifies credentials, and if every thing checks out, serves the consumer the requested file.
The three-tier structure separates the presentation of knowledge, the application logic, and the info storage into three tiers. This structure is generalized into an N-tier mannequin in case it is necessary to further divide the phases composing the applying logic and storage tiers. This mannequin is usually extra scalable than the two-tier one as a result of it is attainable to distribute the tiers into several computing nodes, thus isolating the efficiency bottlenecks. At the identical time, these methods are also extra complicated to understand and handle.
The RIAA can be recognized to have uploaded faux music and flicks to P2P networks in order to deter unlawful file sharing. Consequently, the P2P networks of right now have seen an infinite enhance of their security and file verification mechanisms. When a server experiences an increase in load it redirects incoming friends to different friends who have agreed to reflect the content, thus off-loading steadiness from the server. This system makes use of the truth that the bottle-neck is more than likely in the outgoing bandwidth than the CPU, hence its server-centric design.
Having one of the best surroundings, this structure assists the person interface to store on the consumer aspect and database on the server gadget. The business logic and database logic are maintained both on the consumer aspect or on the server’s aspect. This structure is faster than 1 tier architecture as it does not have any middleman between the consumer and the server. The greatest example of 2 tier structure is the net ticket reservation system the place there should be no confusion between two clients. The limitations of this framework are much less safety, and more users affects the performance of the system.
Peer-to-peer computing or networking is a distributed application structure that partitions duties or workloads between friends. Peers are equally privileged, equipotent individuals within the network. In shopper server computing, the shoppers requests a useful resource and the server offers that resource. A server may serve a number of purchasers at the identical time while a client is in contact with just one server. A server is a computer or system that provides sources, data, companies, or programs to other computer systems, often recognized as clients, over a network. An particular person system can present sources and use them from one other system at the similar time.
For peer-to-peer methods, pure implementations are very exhausting to seek out and, as mentioned for the case of Kazaa, evolutions of the model, which launched some kind of hierarchy among the many nodes, are widespread. The Client-server structure helps us to speak information with other computers, and devices, organizations. A networking model contains client-server structure that allows multi-user updates by way of a graphical consumer interface to a shared database. Large and small companies leverage networking to grow and digitize their operations, advertise their items, and higher perceive news and occasions specific to their sectors. The centralized network has whole management over the activities and operations.
What Are The Components Of A Client-server Model?
Internet service suppliers have been identified to throttle P2P file-sharing visitors because of its high-bandwidth utilization. In October 2007, Comcast, one of many largest broadband Internet providers in the United States, started blocking P2P purposes such as BitTorrent. Their rationale was that P2P is usually used to share illegal content, and their infrastructure just isn't designed for continuous, high-bandwidth site visitors. The client–server mannequin provides monetary barriers-to-entry to small publishers and people, and may be less efficient for sharing massive recordsdata.
The final line of the envelope incorporates the command DATA on its own. This tells the server that any text following this command would be the body of the text message. Dimension of the data to take care of, manage, and entry, which could be prohibitive for a single computation node or too giant for serving the clients with passable performance. File servers retailer recordsdata in a centralized location so that everyone in a company has equal access to resources.


No comments:
Post a Comment